The SFTP is Secure Shell Data Stream. It provides a secure connection and file transfer protection.
SFTP Chroot Jail in particular restricts Linux Directory user-wise access. The Linux administrator manages server and SFTP user access to a few files through the directory.
Users can log in to SFTP, SSH, or SCP.
Step 1:- Creating an SFTP Group
Login via SSH
Create a new SFTP group
Enter this command :
sudo groupadd sftpgroup
Step 2 - Adding Users to SFTP Group
The next step is to create a new user. user doesn’t exist you can create a new user account by typing:
sudo useradd -g sftpgroup -s /bin/false -m -d /home/username username
The -g sftpgroup option will add the user to the sftpgroup group.
The -s /bin/false option sets the user’s login shell. The user will not be able to log in to the server via SSH.
The -m -d /home/username options tell useradd to create the user home directory.
You will set now a strong password using the following command:
sudo passwd username
Otherwise if the user you want to restrict already exists, add the user to the sftpgroup and change the user’s shell:
sudo usermod -G sftpgroup -s /bin/false username2
Root must be the owner of the home directory with 755 permission:
sudo chown root: /home/username
sudo chmod 755 /home/username
Users will not be able to create new files and directories as their home directories are owned by root.
As there are no directories in the user's home, you will have to create the following directories:
sudo mkdir /home/username/{public_html,uploads}
sudo chmod 755 /home/username/{public_html,uploads}
sudo chown username:sftpgroup /home/username/{public_html,uploads}
These changes may lead to permission issues if a web application is using the user’s public_html directory as the document root.
Step 3: - Configuring the SSH
Next one is SSH configuration file with editor /etc/ssh/sshd_config
sudo nano /etc/ssh/sshd_config
Now, search for the line Subsystem sftp. It is present at the end of the file.
If starts with a hash #. Then, remove the hash # and modify it to look like below:
/etc/ssh/sshd_config
Subsystem sftp internal-sftp
/etc/ssh/sshd_config
Match Group sftpgroup
ChrootDirectory %h
ForceCommand internal-sftp
AllowTcpForwarding no
X11Forwarding no
The ChrootDirectory directive in %h means the user's home directory.
Now save the file and restart the SSH service.
sudo systemctl restart ssh
Step 4: - Testing the Configuration
sftp username@192.168.10.34
username@192.168.121.30's password:
sftp>pwd
Remote working directory: /
sftp> ls
public_html uploads
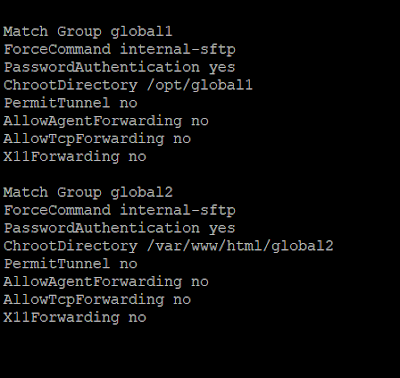
Note:- Different Users or Groups access one or more directories
You can Also Other directories that will jail access possible. You can create a new user and new group.
Then changes in /etc/ssh/sshd_config file.
One or More users and more groups with limited access possible particular directory access with jail access.
Below shown the image;






0 Comments